Finding security vulnerabilities in packages using Composer Audit command
Using third-party packages is a great way to add/implement certain features in your projects. For instance, Composer is the de-facto way of installing third-party packages in PHP-based projects conveniently.
But this convenience comes at a cost. Since your project relies on the code which is written by someone else, this also means it would also bring in security vulnerabilities (if any) to your project. This could prove to be fateful for your project if it deals with sensitive information.
So, this is why it’s important to keep a check on installed packages and whether they have any security vulnerabilities or not.
To mitigate this, Composer 2.4.0 introduced a new command called
composer auditthat checks for known security vulnerabilities in installed packages.
It does this by using the “List security advisory” API provided by Packagist.
To get started, first, upgrade your Composer to use version 2.4.0. Since this version is still a release candidate at the moment, you need to use the following command to try it out.
$ composer self-update --preview
And then you can try using the composer audit command in your project like so.
$ composer audit
Here’s the output when I ran it in my Laravel project.
As you can tell, currently there aren’t any security vulnerabilities in the packages I’m using.
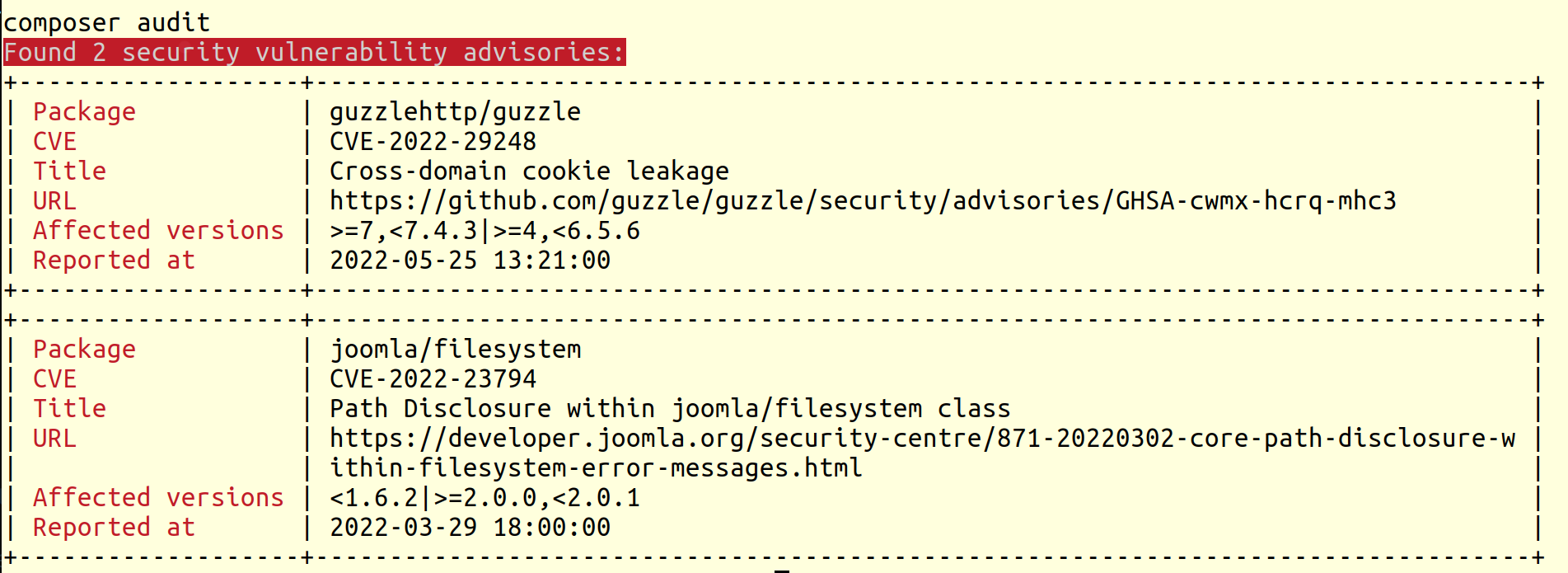
But if there are any vulnerabilities, here’s what the output looks like.
👋 Hi there! This is Amit, again. I write articles about all things web development. If you enjoy my work (the articles, the open-source projects, my general demeanour... anything really), consider leaving a tip & supporting the site. Your support is incredibly appreciated!



